- HOME
- Email security gateway: What is it and how does it work?
Email security gateway: What is it and how does it work?
- Last Updated : July 30, 2025
- 337 Views
- 6 Min Read
There once was a time when every email was precious. Opening every email was a near-magical experience.
That time has long passed.
Email inboxes are now overwhelmed with spam, unrequested contact from marketers, and cyberthreats. Every email has to be carefully examined for potential security threats, viruses, and data breaches. Worse, because so much business communication happens over email, there’s always a risk that an employee will share sensitive information with the wrong recipient, leading to a security breach.
Email security gateways are essential for defending your organization from these threats. Here’s why.
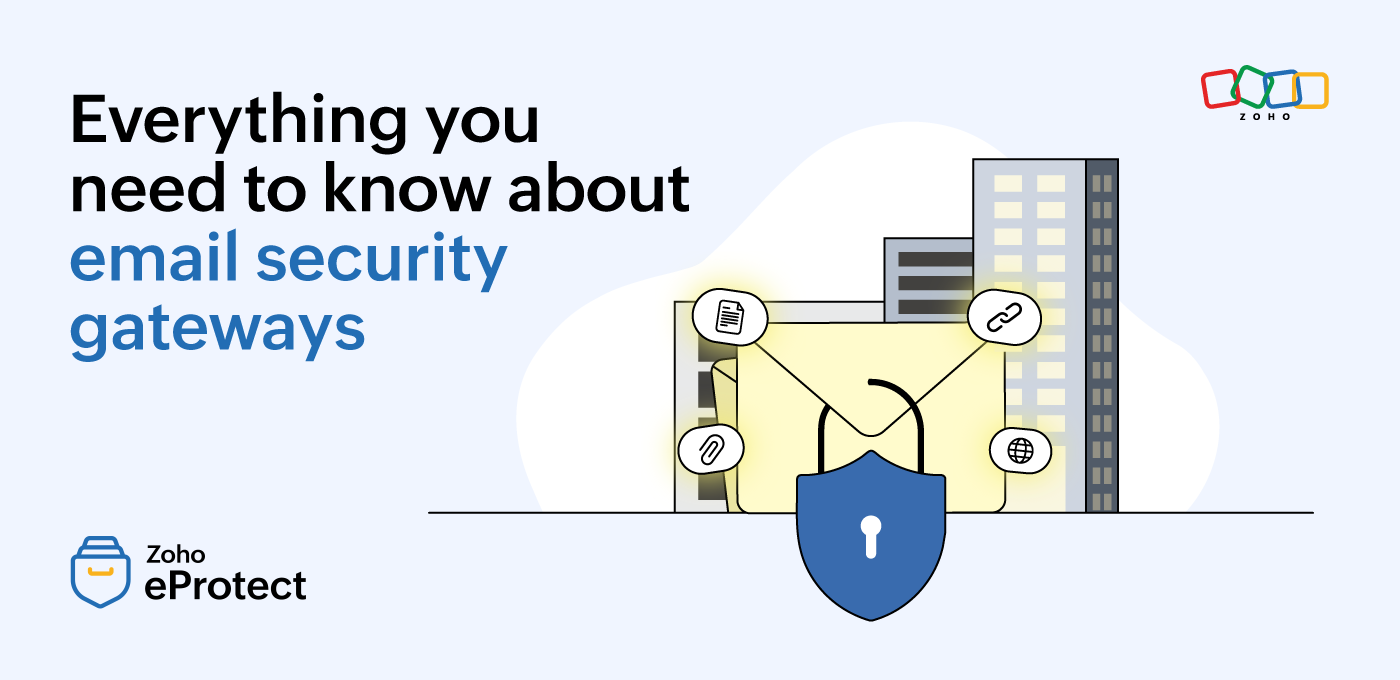
How email security gateways work
An email security gateway, often referred to as a secure email gateway or SEG, is an application dedicated to preventing common data breaches, infections, and other security issues that originate from emails an organization sends and receives. These tools are distinct from email clients, which handle the actual drafting, sending, and storing of emails. Most email clients have some type of built-in security for combating common security risks, but they aren’t as robust as dedicated email security gateways.
According to Gartner’s 2025 Magic Quadrant for Email Security Platforms report, email security gateways need the following features:
- Message, body, and header scanning for detecting spam and phishing.
- Attachment inspection and quarantine (or disarming).
- URL analysis and protection.
- Email data protection, encryption, and data loss prevention.
Additionally, while not mandatory, these features are common among such platforms:
- Domain-based Message Authentication, Reporting & Conformance (DMARC)
- DomainKeys Identified Mail (DKIM)
- Sender policy framework (SPF) management
- Account takeover prevention
- Collaboration or productivity tool protection
- Awareness training
- Message transfer agent
Think of an email security gateway as an extra layer of security over your email client, constantly searching for threats while also actively preventing them.
Common email threats in the modern business landscape
In organizations with hundreds or thousands of employees, there are just as many—if not more—opportunities for data breaches, hacking, account takeovers, and other security issues. All of them can have massive repercussions, tarnishing a company’s brand, driving customers away, or triggering significant legal action.
Many of these issues can be triggered by a single email, which is why email security gateways are so crucial. Here are some of the most common—and damaging—threats lurking in your email inbox.
Phishing
A phishing attack is a scam in which a malicious actor passes themselves off as a legitimate entity to try and acquire sensitive information like login credentials, bank details, credit card numbers, or classified information. These attacks can be as elaborate as spoofing an official email address (like a bank’s), building a fake website imitating a login screen, or linking to a fake email encouraging you to log in. Through this attack, an employee may be duped into providing login credentials for a business bank account, giving scammers full access to it.
A phishing attack can also be as simple as someone pretending to be your organization’s CEO, emailing every employee and asking for the company’s credit card number for an urgent purchase.
Malware and viruses
Malware (or “malicious software”) is any type of software designed to harm your devices or data. There are many different types of malware that can be used to steal data, get access to your network, damage devices, or steal login credentials and financial information. Malware can be delivered through email as an attachment or a URL, which will run the software when clicked.
A virus is a type of malware that, much like the biological agent it takes its name from, infects a file (or an entire computer) and spreads from there. Once a virus infects a file, it might spread through other files by copying itself over and over. It might also move from device to device over your network, through shared peripherals like USB drives, or through email.
Social engineering
Think of social engineering as hacking without any machines or files. Through social engineering, a malicious actor may convince an employee to release sensitive information, share login credentials, or even give them access to your network. Instead of sending malware or using similar methods, they will prey on an employee’s empathy and trust to get what they want. Examples of social engineering attacks include:
- Pretending to be an employee who has lost access to an important tool and claiming they need urgent access.
- Threatening an employee with being fired or other repercussions if they don’t immediately share sensitive information.
- Doing an employee “a favor” and using this as leverage to get access to your network.
Sensitive data leaks
Not all email threats begin in the emails your employees receive. Sensitive data leaks can happen when employees accidentally or unknowingly send information that shouldn’t be sent over email. This may be done in the context of their regular, day-to-day work because they don’t understand that some information should never be shared over email. It can also happen with processes or data they aren’t used to handling, meaning they’re not aware of the security requirements they’re expected to follow.
A leak can happen when an email is sent to the wrong person, the wrong attachment is added to an email, a disgruntled ex-employee doesn’t have their email access revoked in time, and more.
Unintended recipients
Accidentally sending an email to the wrong recipient is an easy mistake to make. But when your organization sends sensitive information back and forth repeatedly, a single mistake can quickly balloon into a larger security issue. An employee may send a confidential industry report to someone outside your organization who shares a name with a colleague. An email may be sent from the legal team to a customer support agent when it should have been emailed to the CEO. In either case, the email reaches an unintended recipient, and without proper security measures, this can lead to sensitive data being exposed.
The business benefits of dedicated email security gateways
Implementing an email security gateway is a costly, time-intensive process. But when so much of your organization’s communications happen over email, you need to ensure that every bit of information you send is absolutely secure. Here’s why you should consider an email security gateway.
Free services can’t keep up
While email clients like Gmail often include some level of security, and you can find free email security gateways out on the market, they’re rarely enough. Malicious actors are constantly improving the quality of their attacks, meaning any security measures you have in place need consistent updates. Paid email security gateway services are constantly updated to stay ahead of common phishing attacks, malware threats, and more.
Encryption can prevent breaches
Email security gateways typically encrypt outgoing communications, meaning that an intercepted message rarely gives malicious actors much to work with. Without this key feature, any message sent to the wrong recipient or left unattended for even a moment can lead to a significant data breach.
Demonstrable ROI
Email security gateways may represent a significant investment, but their value to an organization is so high that it’s almost incalculable. A serious data breach can cost an organization millions, and most leaders would pay almost any price to prevent this.
Regulatory compliance
As industry-specific compliance requirements consistently increase, so does the investment you have to make to meet them. An email security gateway may not allow an organization to be compliant with every regulation it needs to meet, but it definitely helps meet requirements like GDPR, HIPAA, SOC 2, and more.
Decreased IT burden
The less security infrastructure you have in place, the more your IT department has to pour into responding to every potential threat. Email security gateways automate away much of this burden, meaning your IT team can focus their response on incidents that truly need their attention.
Reputation preservation
A data breach or security issue won’t just cost your organization money. Your brand is at stake, too. By preventing these breaches, an email security gateway can protect you from situations that could cause irreparable damage to your brand.
Business continuity protection
Security breaches can significantly disrupt business operations for hours, if not days. Email security gateways are just one part of a security toolkit that ensures your business is operating normally as much as it can.
Looking forward in email security
Cyber threats are constantly evolving, becoming more sophisticated, more frequent, and more costly. This makes an email security gateway more than just a protective measure; it’s a necessity.
When a single compromised email can lead to devastating financial losses, regulatory penalties, and irreparable damage to consumer trust, the question isn’t whether you should implement email security. It’s how comprehensive that security should be.
Email security gateways provide the multi-layered defense organizations need to stay ahead of malicious actors and the occasional accident. As we look ahead, email security will increasingly leverage artificial intelligence and machine learning to adapt to the unique threats facing your organization over time.
By implementing email security measures from forward-thinking providers, you’re not just preparing yourself for the threats you face today. You’re preparing for the future.
 Genevieve Michaels
Genevieve MichaelsGenevieve Michaels is a freelance writer based in France. She specializes in long-form content and case studies for B2B tech companies. Her work focuses on collaboration, teamwork, and trends happening in the workplace. She has worked with major SaaS brands and her creative writing has been published in Elle Canada, Vice Canada, Canadian Art Magazine, and more.